
Fibonacci retracements crypto
Apply key retracement ratios to pinpoint probable zones of price reversal or continuation within digital asset charts. These mathematical ratios derived from natural sequences provide specific technical levels where buying or selling pressure often intensifies. Recognizing these points enables traders to anticipate potential support floors or resistance ceilings with higher accuracy. Focus on the 23.6%, […]
University blockchain courses
Structured academic programs dedicated to distributed ledger technologies provide learners with rigorous frameworks to master decentralized systems. These offerings range from introductory modules explaining cryptographic foundations to advanced seminars on consensus algorithms and smart contract development. Enrolling in such curricula ensures a systematic progression through theoretical principles paired with practical applications. Higher education institutions increasingly […]
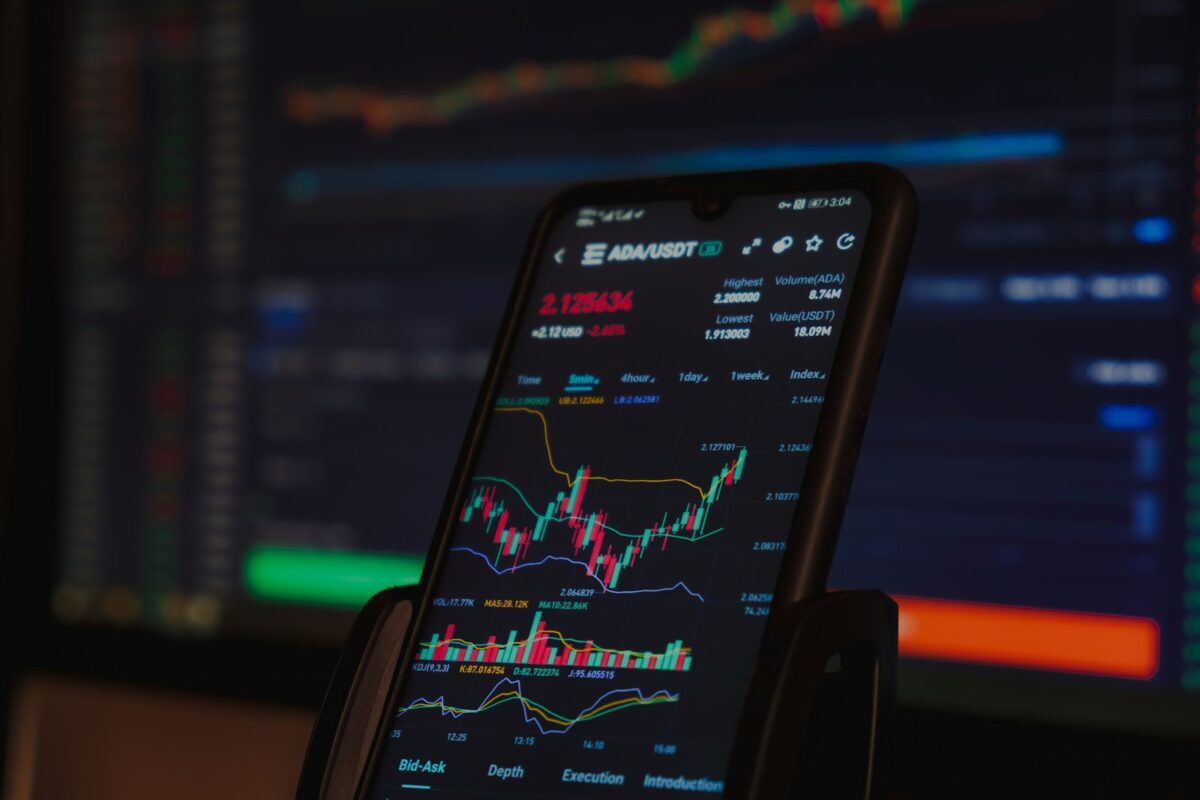
Cryptocurrency dollar cost averaging
Implementing a systematic approach of fixed-amount acquisitions at consistent intervals can significantly reduce exposure to price swings. This method, known as dca, helps investors avoid the pitfalls of trying to time markets and instead emphasizes steady accumulation through repeated purchases. By committing to regular contributions, one smooths out the average expenditure per unit over time, […]
Kyber Network liquidity aggregator
Utilizing a unified on-chain protocol aggregator enhances token swaps by accessing multiple decentralized exchanges simultaneously. This approach optimizes asset conversion rates by sourcing depth from various pools and automated market makers, reducing slippage and improving price execution within a single transaction. The protocol operates entirely on-chain, allowing transparent routing of orders across diverse decentralized venues […]

Understanding blockchain clients
Software implementations designed to interact with decentralized ledgers vary in complexity and functionality. Full nodes perform rigorous validation of all transactions and blocks, ensuring the integrity of the entire chain. In contrast, light clients reduce resource consumption by relying on simplified verification methods, allowing participation without maintaining a complete copy of the ledger. The choice […]
RSI indicator guide
Relative strength evaluation provides a quantitative approach to detect momentum shifts by comparing recent gains and losses over a specified period. The formula generates values between 0 and 100, identifying conditions where an asset may be overbought (commonly above 70) or oversold (typically below 30). These thresholds suggest potential reversal points, enabling tactical entry or […]

Reddit cryptocurrency communities
Engaging with targeted forums on reddit provides direct access to specialized knowledge and real-time support for inquiries related to blockchain tokens. Active subreddits serve as dynamic hubs where participants exchange insights, troubleshoot technical challenges, and clarify complex mechanisms through collaborative discussion. The value of these interactive groups lies in their continuous sharing of verified information […]
MakerDAO decentralized stablecoin
MakerDAO offers a unique approach to maintaining price stability by using a system where assets serve as collateral to generate a cryptocurrency pegged to a fiat value. This mechanism hinges on locking collateral tokens into smart contracts, enabling users to mint the stable asset while securing the system against market fluctuations. Such design ensures that […]

Mirror decentralized publishing
Creators seeking to monetize their writing can leverage NFT technology to establish direct ownership and generate revenue without intermediaries. Tokenizing articles as unique digital assets allows authors to offer limited editions or exclusive content, creating scarcity that fuels demand within a transparent blockchain environment. Crowdfunding integrated with this model enables supporters to invest early in […]

Setting up secure crypto wallet
Selecting the appropriate software for managing your digital funds is the foundational step. Whether you prefer a mobile application or a desktop program, ensure it supports robust encryption and has positive security audits. Prioritize solutions that allow local control over private keys rather than cloud storage. During initialization, generating a seed phrase consisting of 12 […]










