
PleasrDAO NFT acquisition
Direct involvement in decentralized art collectives redefines traditional ownership by enabling shared custody of culturally significant digital assets. This approach transforms how art is valued and preserved, with community-driven groups pooling resources to secure and steward unique digital creations. Such collective models provide a robust framework for maintaining provenance and ensuring transparent governance. The recent […]

Safe technology adoption
Initiate deployment with thorough assessment. Each new system requires detailed evaluation of potential risk vectors before integration. Prioritize security reviews and compatibility testing to identify vulnerabilities early. Comprehensive assessment phases reduce unforeseen failures during rollout. Implement features through gradual introduction. Avoid full-scale launches; instead, activate functionalities incrementally. This approach allows monitoring system responses under real […]

Blockchain formal verification
Applying mathematical rigor to smart contract development provides definitive guarantees about their behavior. Employing specialized tools designed for systematic analysis enables the extraction of proofs that confirm the intended logic and security properties without ambiguity. Such approaches eliminate common vulnerabilities by establishing a formal foundation for contract functionality. Verification frameworks translate contract code into precise […]

Private key management
Control over sensitive authentication elements demands rigorous protocols. Implementing segmented storage solutions–such as hardware modules isolated from networked environments–significantly reduces exposure risks. Employ layered encryption and multifactor authorization to safeguard these credentials from unauthorized retrieval. Adopting proven operational routines enhances the integrity of cryptographic artifacts. Regular rotation schedules, combined with audit trails tracking all access […]

Best crypto books recommendations
“Mastering Bitcoin” by Andreas M. Antonopoulos remains a definitive guide for both beginners and advanced learners seeking to deepen their understanding of blockchain technology and investment strategies. This text offers detailed explanations of the protocol’s mechanics, enabling readers to build practical knowledge rather than relying on surface-level information. For those prioritizing structured education, “The Intelligent […]

Colony collective ownership
Establishing a shared asset model within communal habitats necessitates transparent governance mechanisms that prioritize joint decision-making. This approach relies on distributed management systems where every participant holds a stake, enabling equitable influence over resource allocation and strategic planning. Implementing protocols based on consensus strengthens collaboration and mitigates power imbalances. Operational control within such environments demands […]

Hash functions in cryptocurrency
SHA-256 serves as a foundational algorithm for generating unique fingerprints from data inputs, enabling robust verification processes within decentralized networks. Its deterministic output ensures that any alteration in the original input produces a vastly different signature, reinforcing the immutability of transaction records. These cryptographic algorithms transform variable-length information into fixed-size codes, making it computationally infeasible […]
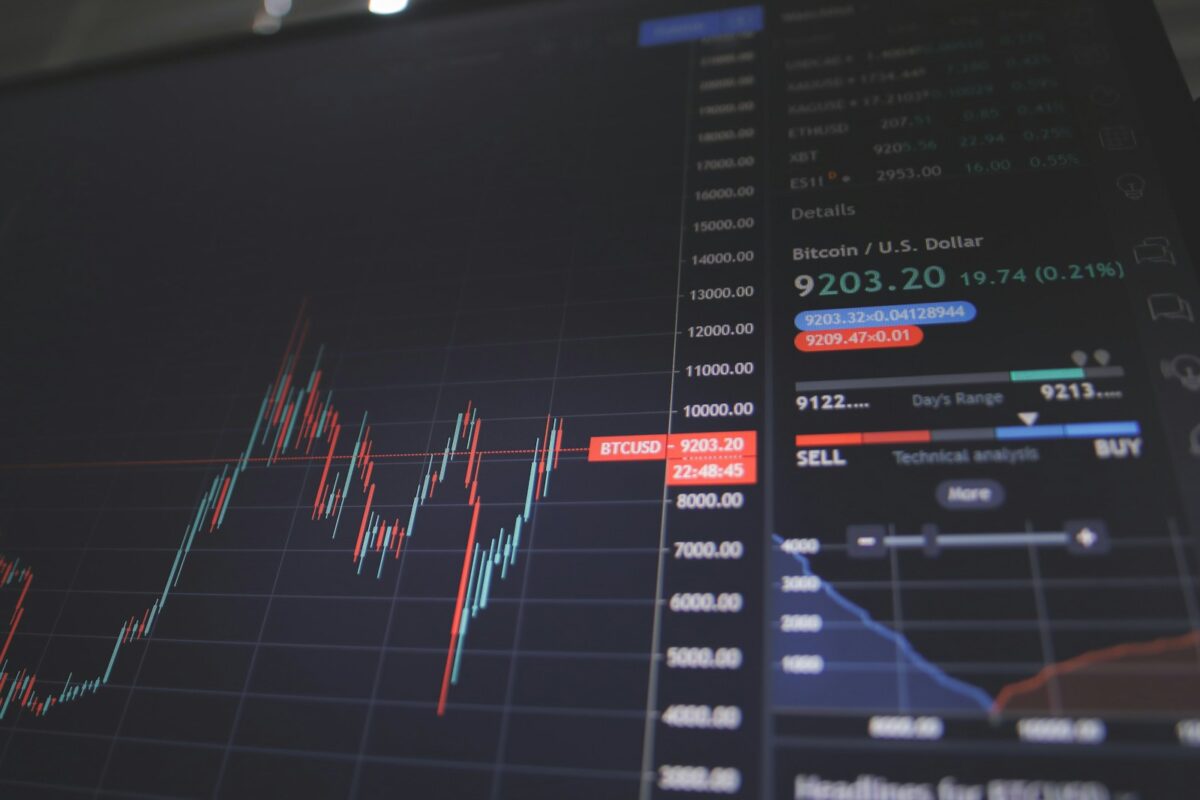
Cryptocurrency fees explained
Transaction expenses vary significantly depending on the type of operation: deposit, withdrawal, or trading. Each action interacts with the underlying network differently, influencing the total cost incurred. For deposits and withdrawals, users often face fixed or percentage-based charges set by platforms, whereas trading costs are tied closely to market liquidity and order types. Gas plays […]

Loopring layer-2 exchange
Scaling Ethereum through zk-rollups enables significant reduction in transaction costs and latency. By aggregating multiple trades off-chain and submitting succinct proofs on-chain, this technology achieves low fees without compromising security or decentralization. The approach enhances throughput substantially compared to native Ethereum transactions. Trading efficiency improves as order settlement happens at speeds unattainable on the base […]
Polynomial commitments blockchain
Succinct proofs enable efficient validation of data without revealing the underlying information, preserving zero-knowledge properties. These proofs drastically reduce communication overhead and computational costs, making them ideal for systems requiring rapid verification with minimal resource consumption. The use of algebraic structures to generate cryptographic commitments allows one to bind data values securely while enabling later […]








