
Cryptocurrency wash trading
Eliminating fake volume is critical for accurate market assessment and investor protection. Artificially inflated activity distorts price signals and misleads participants about real liquidity on exchanges. Manipulation through repetitive self-trades generates misleading statistics that regulatory bodies strive to detect and mitigate with increasingly sophisticated tools. Identifying wash schemes requires analyzing patterns of reciprocal orders executed […]

Understanding blockchain pruning
Full nodes maintain a complete copy of the ledger’s entire history, including all transactional data and intermediate states. This comprehensive storage ensures network security and verifiability but leads to significant challenges in terms of size and storage requirements. As ledgers grow over time, the increasing demand for disk space can hinder participation by resource-constrained operators. […]

Arweave permanent data storage
Utilize the blockweave structure to maintain continuous access to archived content without reliance on centralized servers. This innovative model stores information by linking new blocks with recall of previous ones, enabling efficient retrieval and durable preservation. The permaweb operates atop this foundation, creating a decentralized network that hosts immutable websites and applications. The endowment mechanism […]

Hot wallet security tips
Limit the amount of funds stored in wallets connected to the internet to reduce exposure to theft. Allocating only necessary balances for frequent transactions minimizes potential losses if unauthorized access occurs. Regularly applying software updates is critical for maintaining a strong defense against vulnerabilities. Developers often release patches that close security gaps, so keeping all […]

Cryptocurrency books recommendations
Mastering Bitcoin by Andreas M. Antonopoulos stands out as a definitive guide for learners progressing beyond the basics of blockchain technology and decentralized finance. Its thorough explanations provide both theoretical frameworks and practical applications, making it indispensable for readers seeking advanced knowledge. For those interested in strategic asset allocation within this domain, The Bitcoin Standard […]

Golem decentralized computing
Accessing vast computational resources without centralized infrastructure is achievable by leveraging rental models that connect idle machines worldwide. This approach capitalizes on the sharing of processing capabilities, turning underutilized devices into contributors of a collective network’s strength. Users benefit from scalable power availability, paying only for the exact workload they require. Such platforms utilize a […]
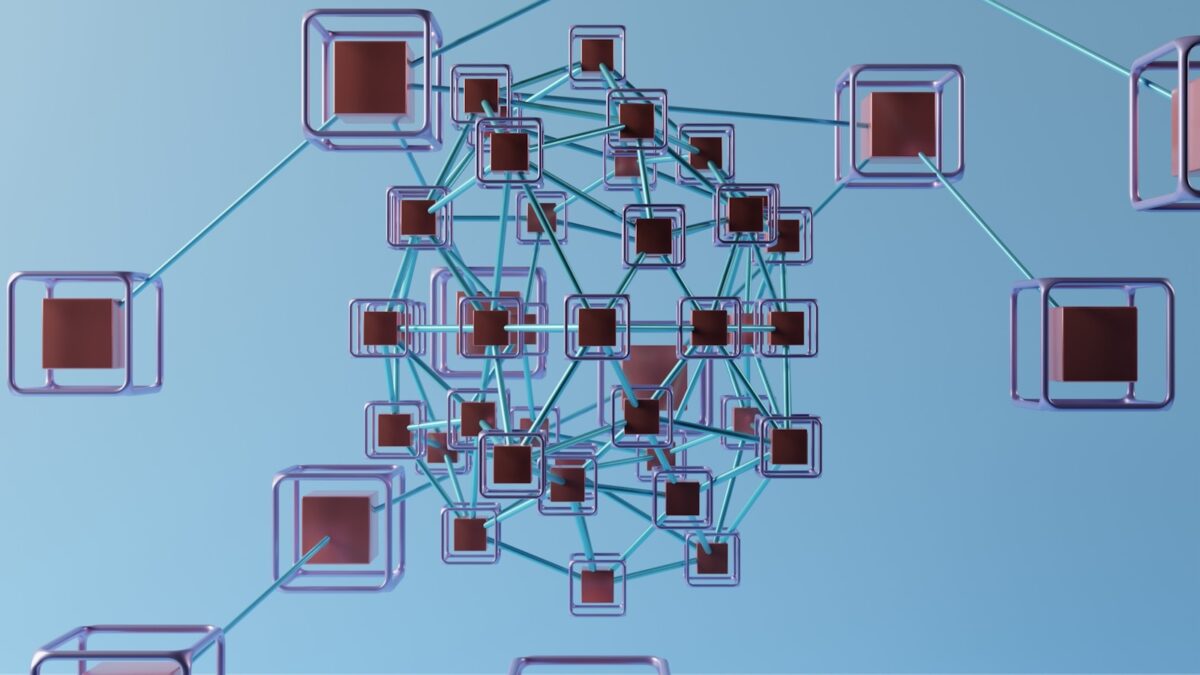
Blockchain merkle proofs
Merkle trees provide a robust structure to verify data integrity with minimal overhead. By organizing data hashes into a binary tree, this method enables light clients to confirm the presence of a specific element through concise evidence rather than downloading entire datasets. The hierarchical arrangement reduces verification complexity from linear to logarithmic scale, significantly enhancing […]

Cryptocurrency arbitrage opportunities
Identifying price differences across multiple trading platforms remains a powerful strategy to generate profit by capitalizing on market inefficiencies. When the same asset trades at varying values on distinct exchanges, executing simultaneous buy and sell actions can yield immediate gains without exposure to directional market risk. Success depends on rapid detection of discrepancies and swift […]

Bitcoin vs traditional money differences
Decentralized systems operate without a central authority, which is the defining characteristic of bitcoin. Unlike fiat currency issued and regulated by governments through centralized banking institutions, this cryptocurrency functions on a distributed ledger called blockchain, allowing peer-to-peer transactions without intermediaries. The physical aspect of conventional cash contrasts sharply with the purely digital nature of this […]

Crypto Twitter accounts follow
Identifying key voices in the cryptocurrency space requires tracking real-time updates from industry experts and prominent influencers. These profiles provide rapid dissemination of market analysis, breaking news, and technical insights that shape investment decisions. Subscribing to a curated list of such sources ensures timely access to reliable information streams without noise. Advanced tools enable continuous […]





