
Buying Bitcoin step by step
Initiate the acquisition process by selecting a reliable exchange that supports your preferred payment methods. Ensure the platform offers transparent fees and robust security measures. This foundation guarantees smoother transactions and protects your assets from potential risks. Complete the necessary verification procedures before proceeding with any purchase. Most exchanges require identity confirmation through documents or […]

Long-term security planning
Integrating adaptive frameworks within systems ensures resilience against technological shifts. Prioritize modular architectures that accommodate iterative upgrades without compromising integrity, thus enabling continuous adaptation alongside emerging threats. Future-proofing demands anticipation of evolutionary trends in both tools and tactics. Employ predictive analytics combined with scenario modeling to identify vulnerabilities before exploitation becomes feasible, allowing for proactive […]

Online crypto courses comparison
For acquiring practical skills and recognized certification in blockchain technology, selecting a platform with structured learning pathways is paramount. Programs that balance theoretical foundations with hands-on experiments accelerate conceptual clarity and technical proficiency. Prioritize offerings that provide modular content progression, enabling focused development from fundamental principles to advanced applications. Certification validity should align with industry […]
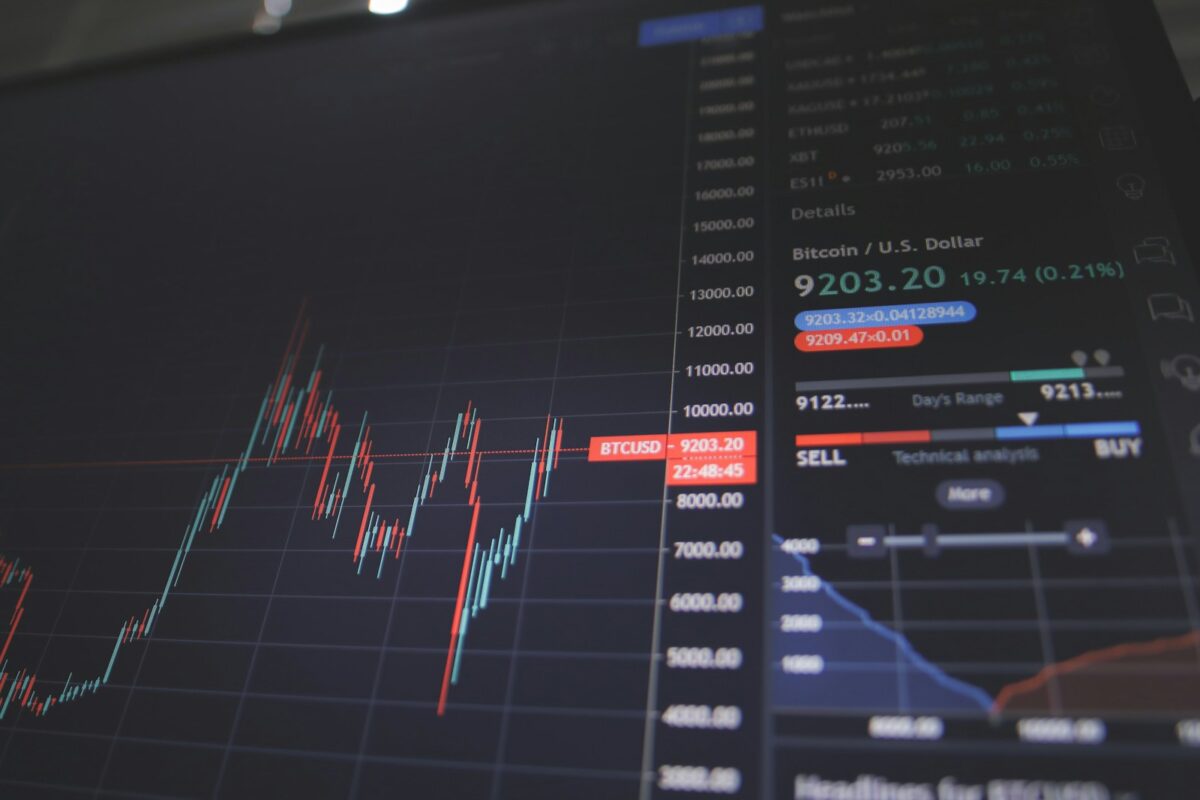
Safe crypto gifting
Thorough examination of legal implications is imperative before initiating any transfer of digital tokens as presents. Jurisdictions differ significantly in how such transfers are classified–ranging from gifts to taxable events–and understanding these distinctions protects both sender and recipient from unexpected liabilities. Security protocols must be prioritized to safeguard transferred assets. Employing hardware wallets, multi-signature authorizations, […]

Alpha Finance DeFi
Leverage amplifies yield opportunities in decentralized protocols by enabling users to borrow assets and increase their exposure to farming strategies. Utilizing a platform like Homora, participants can execute leveraged farming positions that boost returns beyond simple yield farming techniques. Lending within this ecosystem functions as the backbone for leverage, supplying liquidity pools with assets borrowers […]

Uniswap decentralized exchange
Utilize liquidity pools to facilitate seamless token swaps without relying on traditional order books. These pools aggregate assets from multiple contributors, enabling automated market-making through smart contracts. Instead of a maker placing discrete orders, liquidity providers deposit funds into pools that power continuous trading availability. The protocol operates as a decentralized platform where users maintain […]
Blockchain checkpointing mechanisms
Implementing periodic state anchors significantly reduces vulnerability windows, enabling validators to establish long-range finality with greater confidence. By introducing discrete restoration points, the network limits the scope for attacks aiming to rewrite history or exploit consensus ambiguities. These anchors serve as immutable milestones that validators reference to verify chain integrity and prevent rollback beyond confirmed […]
Two-factor authentication for crypto
Activate 2FA using an authenticator app like Google Authenticator instead of SMS codes to significantly reduce vulnerability to SIM swapping and phishing attacks. Authenticator applications generate time-based one-time passwords (TOTP), providing dynamic protection that SMS messages cannot guarantee. Backup codes are indispensable for maintaining access if your primary device is lost or reset. Securely store […]

DYdX derivatives trading
Margin utilization on dYdX enables market participants to increase exposure without full capital commitment, enhancing potential returns while managing risk. The platform supports perpetual agreements that do not expire, allowing continuous position holding with funding rates balancing long and short demand. Such instruments provide flexibility for strategic positioning beyond spot asset ownership. dYdX’s ecosystem offers […]
Algorand pure proof-of-stake
Scalability challenges in decentralized networks demand consensus algorithms that maintain speed without sacrificing security. A purely stake-weighted validation mechanism eliminates many inefficiencies linked to energy-intensive models, drastically reducing the carbon footprint while supporting rapid transaction finality. The consensus protocol under examination leverages token ownership to select validators randomly, ensuring participation aligns with economic incentives rather […]










