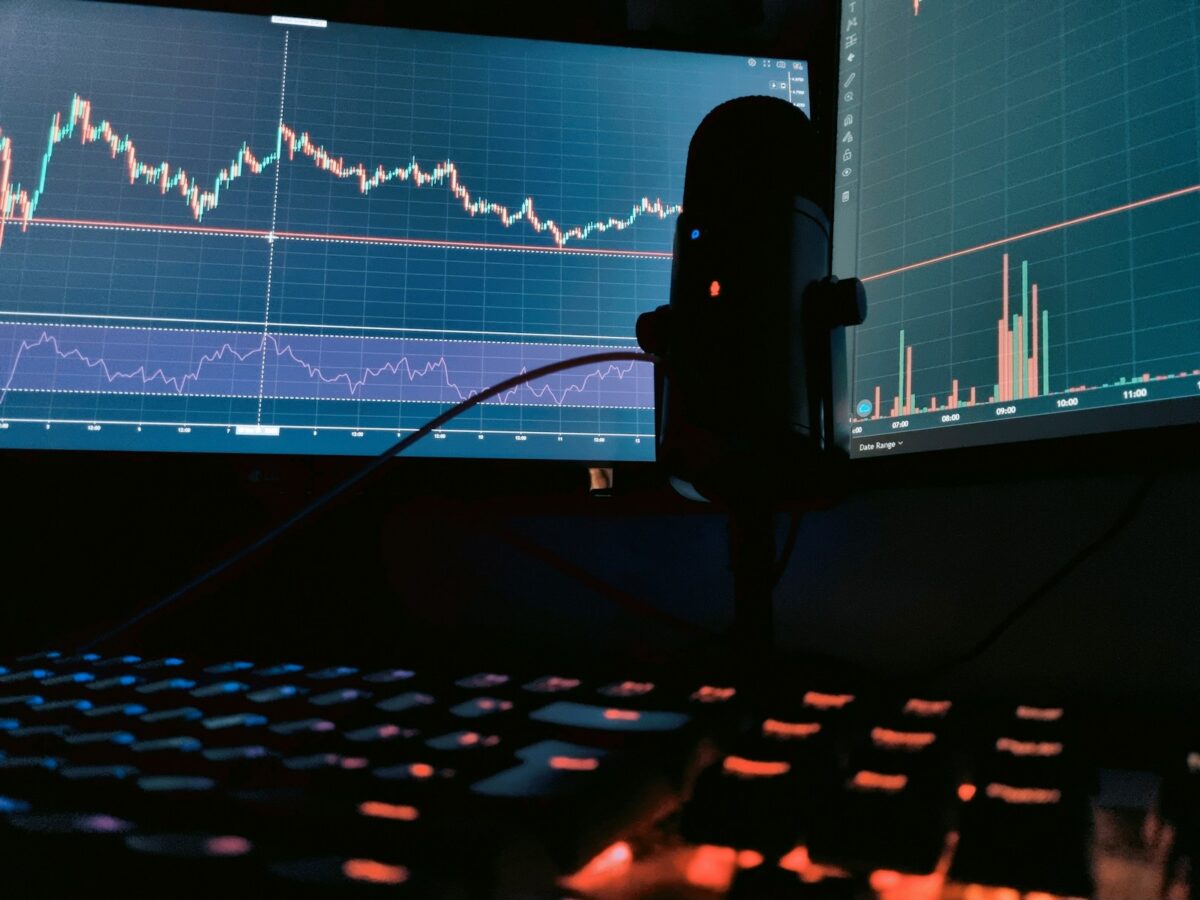
Crypto webinar series
Live presentations led by an expert provide a unique opportunity to examine complex blockchain mechanisms with clarity. Each session is designed to build understanding incrementally, enabling participants to experiment mentally with concepts rather than passively absorb information. The interactive format encourages active involvement, where attendees can pose questions during the Q&A segments and receive targeted […]
DAOstack holographic consensus
Adopting a layered mechanism for collective agreement can drastically improve scalability and accuracy in decentralized organizations. By integrating a holographic approach, systems enable smaller groups to predict the outcome of broader assemblies, allowing them to allocate attention efficiently while maintaining reliable alignment with the entire community’s choices. This method leverages prediction markets as a core […]

Crypto tax compliance
Maintain thorough records of all transactions involving digital assets to meet legal requirements and ensure accurate reporting of capital gains. The IRS mandates detailed documentation that includes acquisition dates, cost basis, sale prices, and the nature of each transaction. Failure to provide precise data can lead to audits and penalties under federal law. Calculate gains […]

Convex Finance yield optimization
Allocating CRV tokens into strategic staking pools offers a direct path to enhancing passive income streams through boosted reward mechanisms. By carefully selecting vaults that amplify rewards distribution, participants can significantly increase their token accrual rates beyond basic staking returns. Advanced approaches involve leveraging platform-specific boosting features, which multiply incentives based on locked positions or […]

PancakeSwap Binance Smart Chain
For users seeking high yield opportunities, this platform offers advanced farming options that maximize returns by leveraging liquidity pools built on a widely adopted blockchain ecosystem. Its decentralized exchange (dex) infrastructure ensures swift and cost-efficient swaps, supporting an extensive range of tokens native to this network. Integrating smart contract-based lottery mechanics introduces an engaging layer […]

Crypto custody education
Managing private keys independently reduces reliance on third-party providers, minimizing exposure to external risks. Understanding the mechanisms behind direct digital asset governance empowers individuals and institutions to implement robust protection strategies tailored to their needs. Effective key handling involves rigorous protocols for generation, storage, and recovery. Experimental approaches such as multi-signature schemes and hardware isolation […]
WAX gaming blockchain
Choose platforms with minimal transactional costs to maximize the value of digital item exchanges. Networks offering low fees enable frequent trading and interaction without significant financial barriers. This efficiency is particularly important for virtual collectibles and NFTs, where high charges often deter active participation. Prioritize environmentally responsible infrastructures that maintain carbon neutrality. The ecological impact […]
Graph protocol data indexing
Efficient querying of blockchain events requires structuring decentralized records into accessible formats. Developers utilize specialized APIs that transform raw chain logs into organized entities, enabling rapid searches and filtered retrievals. These APIs serve as gateways for dApps seeking to interact with complex on-chain activity without direct node management. Subgraphs represent tailored data schemas designed to […]

Blockchain transparency benefits
Open ledgers enable unmatched clarity by allowing every transaction to be publicly visible and easily traceable. This unrestricted access transforms how data is recorded, making it possible to verify records independently without reliance on a single controlling entity. Such visibility increases accountability by exposing actions to continuous scrutiny, reducing opportunities for manipulation or fraud. The […]
Decentraland virtual world
Decentraland represents a fully immersive experience where users acquire digital property known as land, secured through blockchain technology. Each parcel functions as a unique NFT, granting ownership rights and enabling creative development within this expansive simulation. Managing these assets requires MANA, the native cryptocurrency facilitating transactions and governance. The platform operates on principles of shared […]