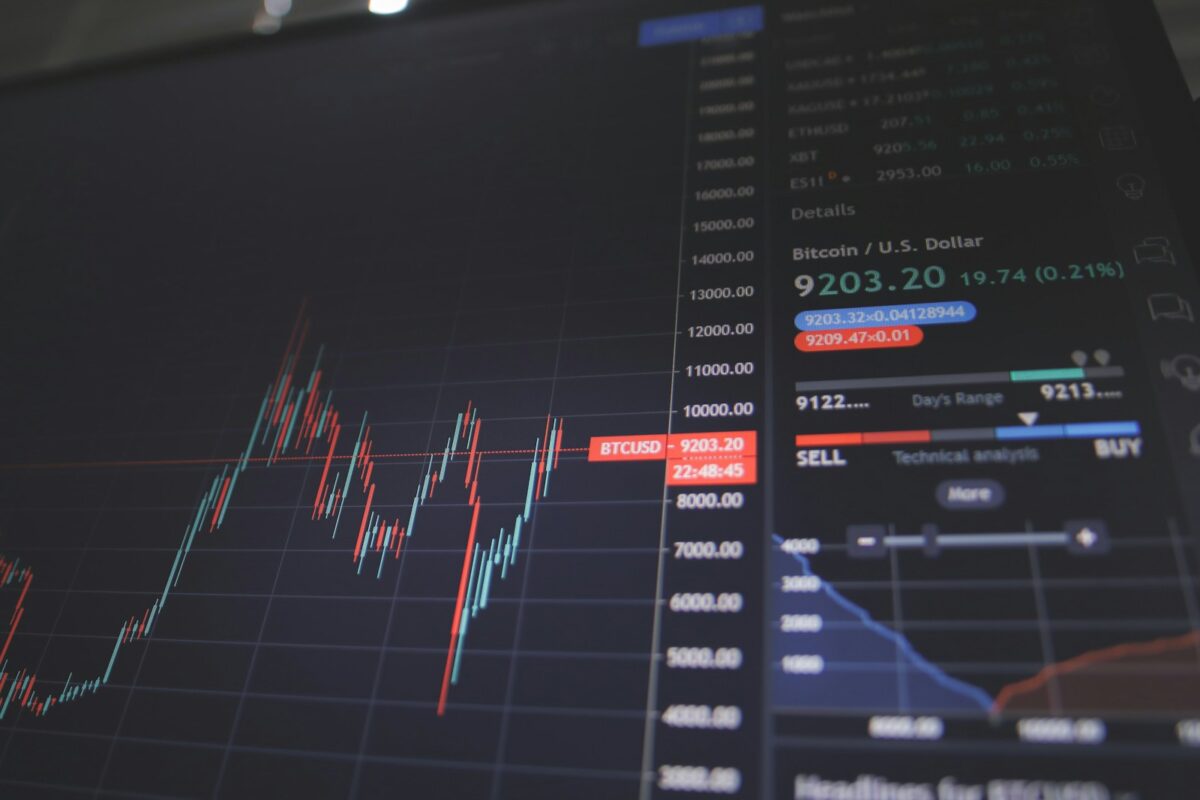
Understanding blockchain epochs
Epochs function as defined periods within consensus protocols that organize the sequence of validator activities and state transitions. Each cycle segments time into manageable intervals where specific sets of validators are assigned responsibilities for transaction validation and block proposal. This structuring enhances network stability by ensuring orderly distribution of tasks across these temporal partitions. The […]

Crypto news sources
Coindesk remains a leading platform delivering timely updates and in-depth analysis on blockchain developments. Its structured reports combine market data with investigative research, offering readers comprehensive insights into network changes and regulatory impacts. Cointelegraphreliable platforms that provide factual updates and in-depth analysis is fundamental. Trusted outlets such as Cointelegraph and Coindesk stand out by delivering […]

Safe arbitrage trading
Verification of all platforms involved in cross-market activities is mandatory before allocating any capital. Confirming the legitimacy and compliance of exchanges reduces exposure to fraud and technical failures. Utilize multi-factor authentication and ensure identity checks are consistently enforced to maintain high security standards throughout the process. Implementing robust protection mechanisms against market manipulation and sudden […]
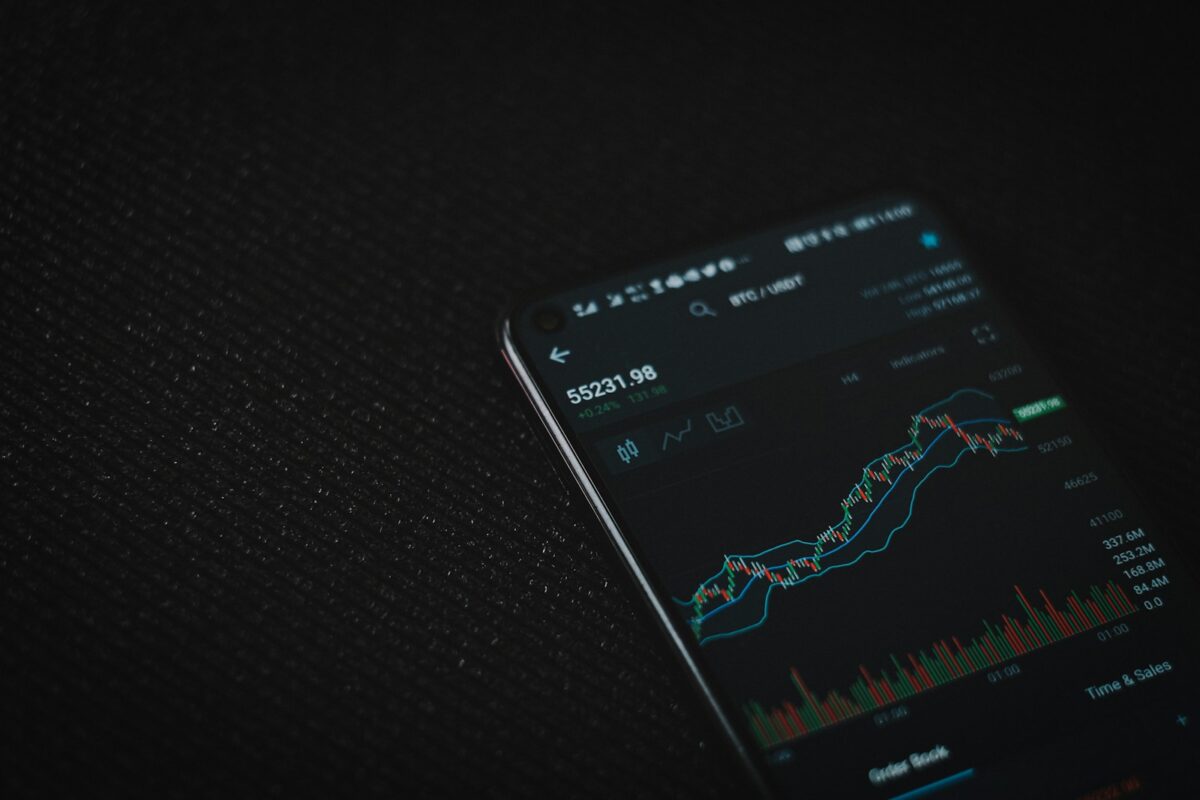
Mobile wallet security tips
Enable automatic updates for your payment app to ensure the latest patches and improvements are installed without delay. Developers regularly release fixes addressing vulnerabilities that can otherwise be exploited. Lock your device screen using strong PINs, patterns, or biometric authentication. This simple measure prevents unauthorized access and adds a critical barrier before anyone can open […]

Blockchain interoperability solutions
Bridges represent a pivotal mechanism enabling seamless communication between different ledgers within the decentralized ecosystem. By translating and validating transactions across varying standards, these connectors facilitate data and value transfer without compromising security or decentralization. The design of robust bridges requires addressing challenges such as latency, trust assumptions, and consensus alignment to ensure accurate synchronization […]
Crypto vs gold comparison
Choosing between a digital store of value and a tangible precious metal as an investment requires careful evaluation of their roles in hedging against inflation. Unlike physical commodities, decentralized digital assets offer high liquidity and ease of transfer, yet lack centuries-long stability records inherent to metals. Investors seeking protection from currency devaluation must weigh these […]

Building crypto career
Identify specific roles such as developer, analyst, or marketing specialist to target your job search effectively. Developers focusing on blockchain protocols require proficiency in programming languages like Solidity and Rust, while analysts need strong data interpretation skills and market understanding. Marketing professionals benefit from expertise in community management and digital campaigns tailored to decentralized platforms. […]
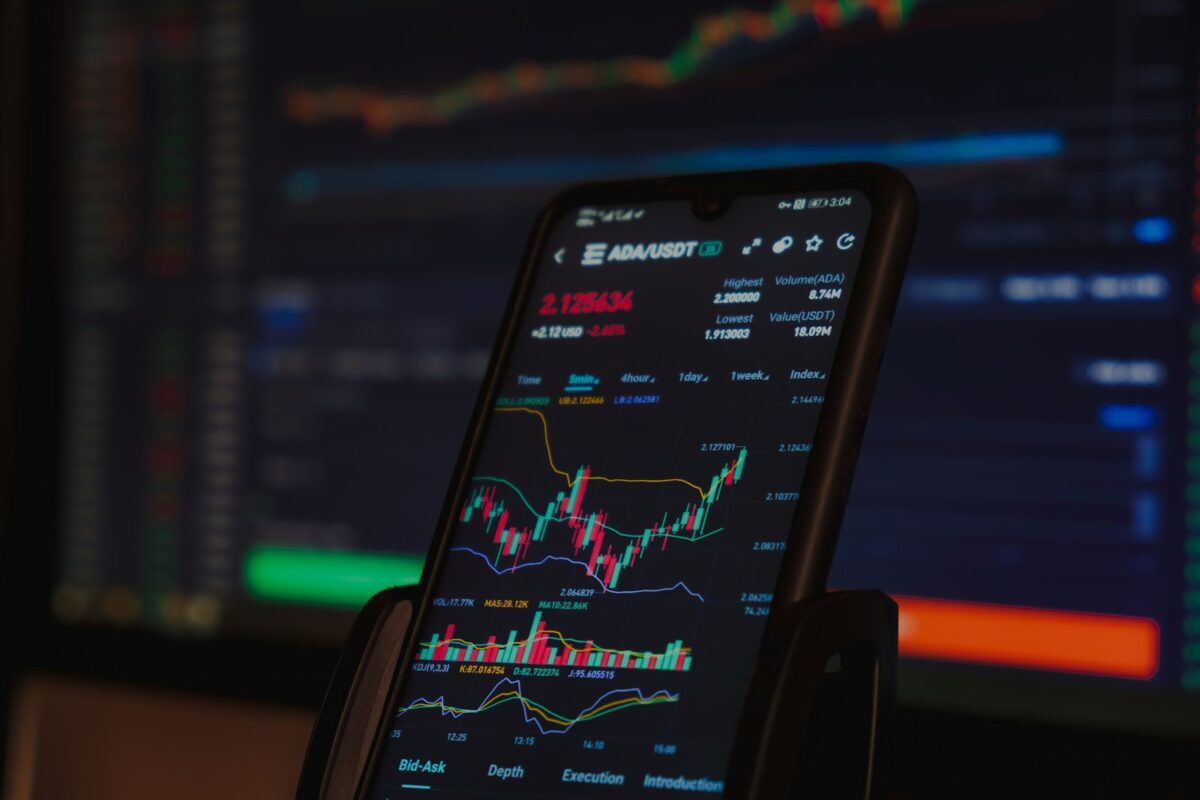
NFT fundamentals explained
Ownership of unique digital assets relies on standardized tokens that verify authenticity and provenance. Each token contains metadata encoding distinct properties, making it impossible to interchange with others. These standards define how assets are created, transferred, and stored securely on blockchain networks. The use of metadata embedded in tokens allows marketplaces to display detailed information […]

Secure wallet recovery
The most effective method for restoring control over your asset storage involves securely preserving a unique backup phrase. This sequence of words serves as the primary key to access and reestablish entry when standard authentication fails or devices become inaccessible. During the restoration procedure, correctly entering this phrase is critical; any alteration or loss compromises […]

Chainlink oracle network
Utilize decentralized data providers to enhance smart contracts with trustworthy external information. This system bridges on-chain applications and off-chain realities by delivering reliable real-world data feeds directly into programmable agreements. By integrating multiple independent sources, it mitigates single points of failure and strengthens data integrity for decentralized finance (DeFi) protocols and beyond. The infrastructure operates […]